What Is The Encryption Mechanism That Is Used With The Wpa2 Security Standard?
In wireless security, passwords are only half the battle. Choosing the proper level of encryption is simply equally vital, and the right choice will decide whether your wireless LAN is a firm of harbinger or a resilient fortress.
Most wireless access points (APs) come up with the ability to enable one of four wireless encryption standards: Wired Equivalent Privacy (WEP), Wi-Fi Protected Admission, WPA2 or WPA3. Find out beneath which is best for your wireless security needs.
Enterprises can employ this side-by-side comparison of the iv security protocols to explore which ane they should employ in their wireless networks and when. This article likewise takes a deep dive into the history and technical details of WEP, WPA, WPA2 and WPA3.
WEP, WPA, WPA2 and WPA3: Which is best?
When choosing from among WEP, WPA, WPA2 and WPA3 wireless security protocols, experts concord WPA3 is all-time for Wi-Fi security. Equally the most upwards-to-date wireless encryption protocol, WPA3 is the well-nigh secure choice. Some wireless APs practise non support WPA3, however. In that case, the next best option is WPA2, which is widely deployed in the enterprise infinite today.
At this indicate, no 1 should use the original wireless security protocol, WEP, or even its immediate successor, WPA, as both are outdated and brand wireless networks extremely vulnerable to exterior threats. Network administrators should replace any wireless AP or router that supports WEP or WPA with a newer device that's compatible with WPA2 or WPA3.
How does WEP work?
Wi-Fi Alliance developed WEP -- the first encryption algorithm for the 802.11 standard -- with one main goal: prevent hackers from snooping on wireless data every bit it was transmitted between clients and APs. From its inception in the late 1990s, however, WEP lacked the force necessary to reach this aim.
Cybersecurity experts identified several severe flaws in WEP in 2001, eventually leading to industrywide recommendations to phase out the use of WEP in both enterprise and consumer devices. Afterwards investigators traced a large-calibration cyber attack confronting T.J.Maxx in 2009 back to vulnerabilities exposed past WEP, the Payment Card Manufacture Data Security Standard prohibited retailers and other entities that process credit card data from using WEP.
WEP uses the RC4 (Rivest Cipher 4) stream aught for authentication and encryption. The standard originally specified a 40-chip, pre-shared encryption central; a 104-bit key later became bachelor after the U.S. authorities lifted certain federal restrictions.
An administrator must manually enter and update the key, which combines with a 24-bit initialization vector (IV) in an effort to strengthen encryption. The small size of the IV increases the likelihood that users will recycle keys, however, making them easier to crack. This characteristic, along with several other security flaws and vulnerabilities -- including problematic authentication mechanisms -- makes WEP a risky choice for wireless security.

How does WPA work?
The numerous flaws in WEP revealed the urgent need for an culling, but the deliberately dull and careful processes required to write a new security specification posed a conflict. In response, in 2003, Wi-Fi Alliance released WPA equally an interim standard, while IEEE worked to develop a more advanced, long-term replacement for WEP.
WPA has detached modes for enterprise users and for personal utilise. The enterprise mode, WPA-Extensible Authentication Protocol (WPA-EAP), uses more stringent 802.1x authentication and requires the use of an hallmark server. The personal fashion, WPA-Pre-Shared Key (WPA-PSK), uses pre-shared keys for simpler implementation and management among consumers and pocket-size offices.
Although WPA is also based on RC4, it introduced several enhancements to encryption -- namely, the use of the Temporal Central Integrity Protocol (TKIP). TKIP independent a gear up of the following functions to improve wireless LAN security:
- utilize of 256-chip keys;
- per-bundle primal mixing, which generates a unique fundamental for each parcel;
- automated broadcast of updated keys;
- message integrity check;
- larger Four size using 48 bits; and
- mechanisms to reduce IV reuse.
Wi-Fi Alliance designed WPA to exist astern-compatible with WEP to encourage quick, easy adoption. Network security professionals were able to support the new standard on many WEP-based devices with a elementary firmware update. This framework, however, besides meant the security WPA provided was not equally comprehensive as it could take been.
How does WPA2 work?
As the successor to WPA, the WPA2 standard was ratified past IEEE in 2004 as 802.11i. Like its predecessor, WPA2 likewise offers enterprise and personal modes.
WPA2 replaces RC4 and TKIP with two stronger encryption and hallmark mechanisms: Avant-garde Encryption Standard (AES) and Counter Fashion with Cipher Block Chaining Message Authentication Code Protocol (CCMP), respectively. Also meant to be backward-compatible, WPA2 supports TKIP as a fallback if a device cannot back up CCMP.
Adult by the U.S. authorities to protect classified data, AES comprises three symmetric block ciphers. Each encrypts and decrypts data in blocks of 128 bits using 128-, 192- and 256-bit keys. Although the utilise of AES requires more computing power from APs and clients, ongoing improvements in estimator and network hardware take mitigated performance concerns.
CCMP protects information confidentiality past allowing only authorized network users to receive data, and it uses goose egg cake chaining message authentication code to ensure message integrity.
WPA2 also introduced more than seamless roaming, enabling clients to move from one AP to another on the same Wi-Fi network without having to reauthenticate, using Pairwise Master Key caching or pre-authentication.
In 2017, a Belgian security researcher named Mathy Vanhoef discovered a major security flaw in WPA2 -- the key reinstallation assault (KRACK) vulnerability -- that exploits the reinstallation of wireless encryption keys. While WPA2-Enterprise has a stronger authentication scheme using EAP than WPA2-Personal, which uses pre-shared keys, the KRACK vulnerability exists at the encryption stage and so affects all WPA2 implementations.
A new Wi-Fi network connection begins with a cryptographic four-way handshake between an endpoint and AP in which both devices, through a series of back-and-forth letters, prove they know a preestablished authentication lawmaking -- PMK in enterprise mode and PSK in personal mode -- without either one revealing information technology explicitly. Upon authentication, the third step in the four-way handshake involves the AP passing a traffic encryption key to the client. If the endpoint doesn't acknowledge that it has received the key, the AP will presume a connectivity issue, resending and reinstalling it repeatedly. KRACK attackers -- who must be inside concrete range of both client and network -- tin trigger, capture, analyze, manipulate and replay those retransmissions until they are able to determine the cardinal, pause encryption and gain admission to network data.
"The weaknesses are in the Wi-Fi standard itself and not in individual products or implementations," Vanhoef wrote at the time. "Therefore, any correct implementation of WPA2 is likely affected."
Industry analysts widely acknowledged KRACK every bit a serious WPA2 security flaw, with technology providers apace rolling out software patches to mitigate risk until the arrival of the next generation of wireless security. But many experts argued this particular vulnerability would show difficult to exploit in the real world.
"Do patch what yous tin, but don't panic," cybersecurity researcher Martijn Grooten tweeted. "It'due south unlikely to have a big impact on you."
More commonly, the iv-fashion handshake method also makes WPA2 networks with weak passcodes vulnerable to offline lexicon attacks, a type of brute-force attack that involves systematically trying hundreds, thousands or millions of pre-compiled possible passwords, out of earshot of the target network. In this scenario, an attacker might capture a WPA2 handshake, have that information offline and utilise a reckoner programme to compare it confronting a list of likely codes with the goal of finding ane that aligns logically with the available handshake information. For obvious reasons, dictionary attacks are far less probable to succeed against long passwords with combinations of uppercase and lowercase letters, numbers and special characters.
How does WPA3 piece of work?
In 2018, Wi-Fi Alliance began certification for WPA3, the most contempo wireless security standard and the one that experts at present consider the nearly secure. As of July 2020, Wi-Fi Alliance requires all devices seeking Wi-Fi certification to support WPA3.
WPA3 mandates the adoption of Protected Management Frames, which help guard against eavesdropping and forging. It also standardizes the 128-bit cryptographic suite and disallows obsolete security protocols. WPA3-Enterprise has optional 192-bit security encryption and a 48-bit Iv for heightened protection of sensitive corporate, financial and governmental information. WPA3-Personal uses CCMP-128 and AES-128.
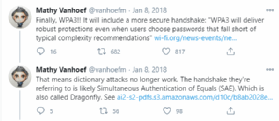
WPA3 addresses WPA2'southward KRACK vulnerability with a more secure cryptographic handshake, replacing the PSK 4-fashion handshake with Simultaneous Authentication of Equals (SAE), a version of the Internet Technology Task Force's dragonfly handshake in which either client or AP can initiate contact. Each device then transmits its hallmark credentials in a discrete, ane-off message, instead of in a give-and-take, multipart chat. Importantly, SAE also eliminates the reuse of encryption keys, requiring a new code with every interaction. Without open-ended communication between AP and client or encryption fundamental reuse, cybercriminals tin can't as easily eavesdrop or insert themselves into an exchange.
SAE limits users to active, on-site authentication attempts, flagging anyone who has exceeded a certain number of password guesses. This capability should make the typical Wi-Fi network more resistant to offline dictionary attacks. Past mandating a new encryption passphrase for each connection, SAE likewise enables a feature called forward secrecy, which aims to prevent attackers who have cracked a passcode from using it to decrypt data they previously captured and saved.
Alongside WPA3, Wi-Fi Brotherhood also introduced a new protocol chosen Wi-Fi Easy Connect, which simplifies the onboarding process for IoT devices that don't have visual configuration interfaces via a mechanism such as a QR code browse. Finally, an boosted feature called Wi-Fi Enhanced Open up makes connecting to public Wi-Fi networks safer past automatically encrypting information between each client and AP using a new unique fundamental.
In practice, of course, WPA3 is not impervious to threats. Vanhoef, the security skillful who discovered KRACK, and Eyal Ronen, a researcher at Tel Aviv University, published several new security flaws in WPA3 in 2019. The then-called Dragonblood vulnerabilities included two downgrade attacks, in which an assaulter forces a device to revert to WPA2, and two side-channel attacks, which enable offline dictionary attacks. Wi-Fi Alliance downplayed the risks, however, maxim vendors could readily mitigate them via software upgrades. Regardless of its potential vulnerabilities, experts concord WPA3 is the most security wireless protocol available today.
This was last published in December 2020
Dig Deeper on Network security
-

Open up System Authentication (OSA)
-

Shared Key Authentication (SKA)
-

WLAN security: All-time practices for wireless network security
-

evil twin attack
What Is The Encryption Mechanism That Is Used With The Wpa2 Security Standard?,
Source: https://www.techtarget.com/searchnetworking/feature/Wireless-encryption-basics-Understanding-WEP-WPA-and-WPA2
Posted by: springerneigne.blogspot.com






0 Response to "What Is The Encryption Mechanism That Is Used With The Wpa2 Security Standard?"
Post a Comment